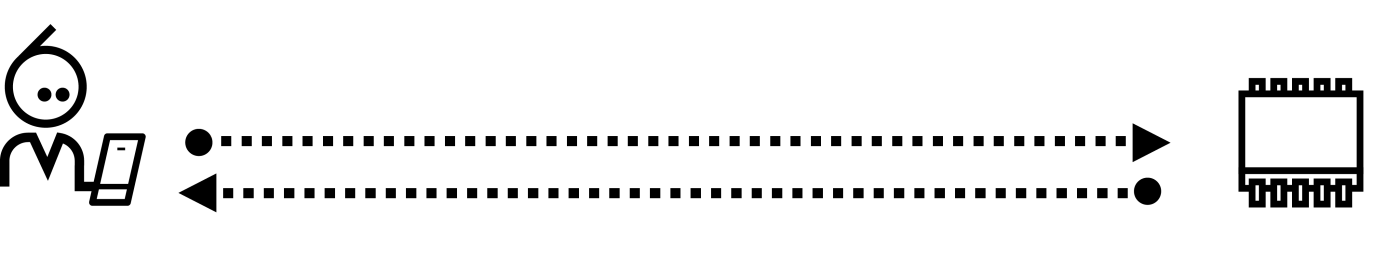
One of the top methods in IoT that provides devices with a safe and secure way to connect to and send data via a network is Transmission Control Protocol (TCP) tunneling. Here’s what you need to know about TCP tunneling, why it matters, and how it works in the world of IoT.
The basics of TCP tunneling
TCP is used as the main data transmission protocol for most network based applications like web applications in a browser, transmitting emails, file transfers and streaming movies. It is also used in many IoT systems already, like on a typical smart video camera. However, using the TCP protocol in its “default” form is inherently insecure. That’s not a big deal if you’re using it on a secure local network, but sending data across the internet via TCP alone is not the best practice.
Plus, when the client and the device are on the same local network, a TCP connection is easily established. But when the two peers are not located on the same network, creating a TCP connection can be a hassle because of the firewalls. A Secure Shell (SSH) tunnel would solve the security issue, but it could still be blocked by firewalls when trying to access a device remotely. The solution is to create a remote TCP tunnel.
TCP tunneling provides secure and direct access to TCP services that are usually inaccessible due to being behind NAT firewalls. It’s essentially a way to reach and use these services smoothly and safely, bypassing the usual network restrictions. To the TCP client and server application, it now looks like the devices are directly connected, but the data is actually tunneled through the internet via the two tunnel endpoints. As a result, the connection can now go through the firewalls.
So in summary, there are three reasons for using TCP tunneling:
- TCP is already the default protocol for many IoT use cases.
- TCP without security handled at the application level (like HTTPS) or without using a secure tunnel is inherently vulnerable.
- Creating TCP connections across NAT / firewall-secured local networks is not possible without a tunneling mechanism.
TCP Tunneling in video streaming
To demonstrate exactly how TCP tunneling works in practice, let’s go through a typical use case. When a client device, like a smartphone, connects to a smart device, like a smart video camera, it can do so in a couple different ways. If the two devices are on the same local network, then they can easily establish a connection so the user can view video footage and send commands to the smart camera.
But things get more complicated if each device connects to a different network and there are firewalls or other intermediaries between them that may block the connection. In this case, TCP tunneling is a way to bypass those intermediaries.
For example, remote home security monitoring is a common IoT application in which the second situation applies, involving different networks and the need for TCP tunneling.
Let’s break down a typical scenario:
Setting: You have a smart security camera system installed at your home. You want to access the camera feed and control the system remotely, say, from your office or while traveling.
Challenge: Your smart security camera is connected to your home’s local Wi-Fi network, which is protected by a firewall for security. Meanwhile, you’re trying to access the camera from a different network – maybe your office’s network, a public Wi-Fi, or your mobile data connection, all of which might also have their own security measures.
Problem: Due to the firewalls and potentially other network security measures in place on both networks, establishing a direct connection between your smartphone and the home security camera can be complex. The security measures, while crucial for protecting the networks, can inadvertently block the data packets that your smartphone sends to the camera and vice versa.
Answer: This is where TCP tunneling comes into play. It creates a secure and dedicated “tunnel” between your smartphone and the home security camera. This tunnel effectively bypasses the firewalls and other network barriers, allowing for a stable and secure connection.
Through a tunnel, data – like live video feed or control commands – can flow seamlessly between your smartphone and the security camera, even though the two devices are on different networks.
TCP tunneling with Nabto
Nabto enables TCP tunneling through the Nabto Edge client SDK. You can integrate the SDK with the existing client application, like a smartphone app, which creates a tunnel endpoint. You can think of an endpoint as the entrance or exit to the tunnel. This starting endpoint (often called the “client” or “source”) is where data first gets put into the tunnel and gets wrapped or encapsulated inside another set of data for its journey.
The finishing endpoint (often called the “server” or “destination,“ in this case the smart device) is where the data exits the tunnel and the Nabto Edge SDK unwraps it to reveal the original data. For example, the smartphone user might want to turn off a video camera so it can be repaired. The command from the smartphone travels through the TCP tunnel to get to the camera. Or the connection can go the other way, when the video camera streams footage to the smartphone.
Both endpoints work together to create and maintain the tunnel and communicate with each other through the Nabto Edge SDK, packaging and unpackaging the data so you can send or receive all information safely and correctly.
TCP tunneling applications
TCP tunneling is ideal for:
- Smart security applications
- P2P video streaming
- Industrial IoT
- Other IoT applications that require low latency and secure connectivity
We’ve already talked about smart home security, so let’s go a little deeper into TCP tunneling specifically for P2P video. Peer-to-peer is a communication method that bypasses a central cloud server and allows two IoT devices to send and receive data directly. The P2P connectivity that Nabto offers is great for applications like video conferencing or streaming live feeds from smart cameras.
In the case of a video conference, participants from all over the world who are connected to different networks can make a direct connection to each other through firewalls via a TCP tunnel. As a result, the video will be high quality and the connection will be reliable and secure.
In the industrial IoT sector, TCP tunneling is useful when you need to transmit sensitive data across the internet or between different parts of a factory or plant. TCP tunneling securely encapsulates and transmits data with minimal latency even through firewalls, which allows real-time monitoring and control in industrial environments.
Some other great applications for TCP tunneling are health care monitoring systems and smart city infrastructure. For example, in health care IoT, patient monitoring devices need to transmit data securely and in real-time to health care providers. TCP tunneling enables this by providing a secure path over potentially unsecured networks, ensuring patient data privacy and timely delivery of critical health data.
In smart city applications, in which various sensors and systems – like smart traffic lights or environmental sensors – need to communicate efficiently, TCP tunneling helps in maintaining a steady flow of data across different network infrastructures.
Final Thoughts
All in all, TCP tunneling provides a high level of security and reliability that many IoT applications need to navigate the complex web of modern networks. For more information on the role of TCP tunneling within IoT, contact us and request a consultation.
Read our other resources
We’ve also published a range of IoT device resources for our community, including:
- Our RTC explainer, which lays out the many benefits of real-time communication for IoT
- IoT and the Future of Video Surveillance, which covers what you can expect to see in smart security applications
- Why Use P2P for IoT Video Streaming?, a guide to why P2P is often the best option for IoT video applications