Machine-to-machine (M2M) technology has been around for a while now. It has fueled automation, brought us accurate weather forecasting and smart homes, and it has also had a profoundly positive impact on the industrial world. So what exactly is M2M and how does it work?
M2M is technology that allows machines to communicate with each other without requiring human intervention. For the most part, this communication is automated. Consider a weather buoy, which can automatically collect data about tides, winds, and temperature and pass it along to a system that automatically processes that data. That’s just one example of M2M.
In a perfect M2M ecosystem, M2M should eliminate data silos by permitting any and all devices within a system to transmit data. Silos occur when data housed in one device or system isn’t easily accessible to other devices and systems. You want to avoid silos because they make communication and analysis much less efficient. So in the ideal M2M world, any devices that collect data, like the buoy that collects data about the tides, should be able to transmit that data to a network of other devices or to a central system. And that communication should happen without requiring a lot of energy or needing to go through a human. In short, the goal of M2M is and always has been to create an increasingly connected world.
M2M from Development to Today
So where did this technology get started? One of the first applications of M2M was basic telemetry, which is still an important part of M2M to this day. Telemetry refers to the collection and long-distance transfer of data, whether through a wired or a wireless connection. Meteorological (weather) data is one early example. Other uses include tracking wildlife for research purposes and monitoring patient vital signs from a central system in a hospital. Telemetry initially relied on telephone wires, radio waves, and other early communications technologies. Now it can also use Wi-Fi and many other modern communication methods.
Next, supervisory control and data acquisition (SCADA) systems came along as another important development in M2M. SCADA systems, which particularly serve the industrial world, collect data, transfer it from a remote location, and allow for entirely remote control of various systems. One of the many tools SCADA systems use is radio frequency identification (RFID), which is another form of M2M based on radio waves. RFID tags are miniature devices that collect and transmit small amounts of data, like location data for tracking, by way of radio waves.
SCADA systems are sometimes used for inventory management to let you know what you have, where it is, and what condition it’s in. They also work for fleet management to keep track of trucks and shipping. Unfortunately, SCADA systems use a lot of different protocols and standards, making it difficult to prevent data silos.
SCADA systems are now being replaced by a more recent development in M2M technology: the Internet of Things (IoT). IoT allows devices to communicate with each other and send data over the internet through Wi-Fi as well as many other protocols and technologies. So you can use IoT devices—a.k.a. smart devices—for modern telemetry, since they can collect and transmit data remotely.
The latest IoT advancements are getting closer to the goal of achieving communication between any devices and across different protocols. Already a single IoT system can use Wi-Fi, Zigbee, Bluetooth, and many other technologies to allow all of the devices within the system to communicate with each other.
How M2M Works
Any form of M2M comes in four parts. The first part is made up of the sensors for gathering data. In a SCADA system, these could be temperature gauges, RFID tags, and other technologies. In an IoT system, these could be smart devices like a smart thermometer or the motion sensors in a smart security system.
The second component of M2M is some method for transferring that data. Many M2M systems use cellular networks for real-time data transfer over long distances. Wi-Fi provides a method for both long-distance and local data transfer, and connectivity protocols like Zigbee, Bluetooth and the upcoming Thread protocol allow for efficient short-range communication between devices. IoT systems generally transfer data through cloud servers. There are also peer-to-peer (P2P) connectivity platforms like Nabto that allow direct communication between devices, bypassing the cloud layer. This tends to be faster and more efficient than a server-based system.
The third component would be a method for storing, reviewing, or analyzing that data. In a cloud system, this is usually a cloud database platform for storage and a business intelligence (BI) platform for analyzing data.
The fourth component is a method for acting on that data. This is what actuators are for. Actuators automatically respond to the data to perform an action. One example of an actuator is the internal electric switch in a smart heater, which could turn the heater on or off automatically depending on the information received from the sensors in the IoT system.
M2M vs. IoT
If you’re very familiar with IoT, then the descriptions of M2M and IoT probably sound quite similar. M2M means automated communication between machines, systems, and devices, whether through a wired or a wireless connection. IoT means lots of devices connecting to each other, usually over the internet, in order to transfer data. M2M systems have sensors, a communication method, some form of data stack, and actuators. IoT systems also have sensors, a communication method, some form of data stack, and actuators. So what exactly is the distinction between the two?
You can think about IoT as being just one method within the larger world of M2M. In other words, IoT is a subset of M2M technology. IoT relies on the concepts of machine-to-machine communication, but not all M2M technology is part of IoT. M2M covers a lot of different systems and protocols, including IoT, SCADA, and basic telemetry. So M2M goes far beyond smart devices.
You can see the relationship between M2M, IoT, SCADA and telemetry below:
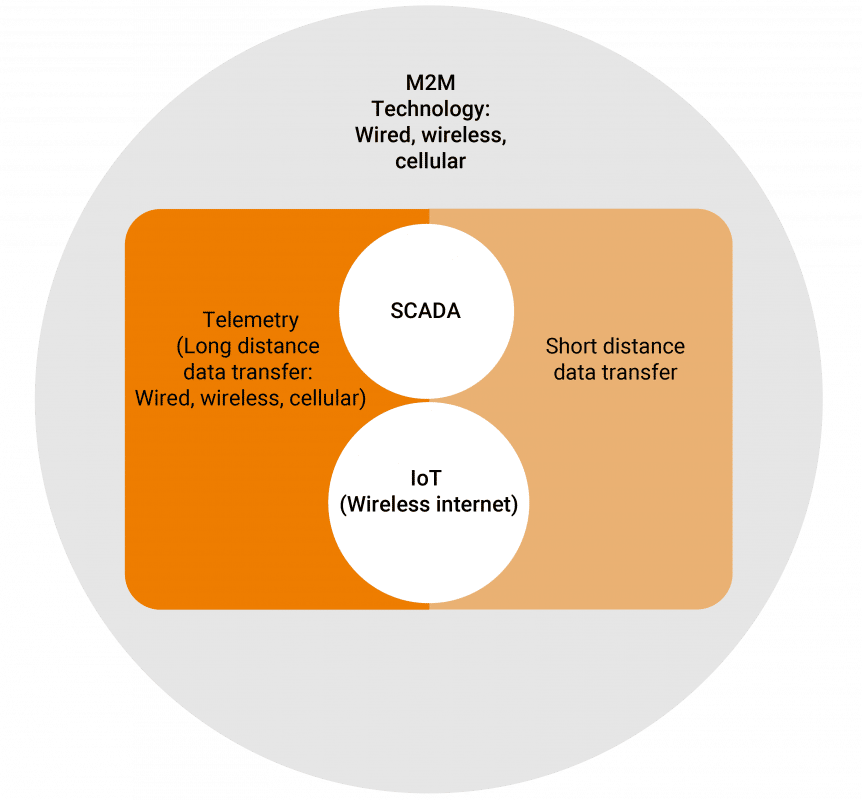
M2M components can communicate through wired, cellular, or wireless connections. By contrast, IoT (which is an abbreviation of Internet of Things) systems rely solely on IP-based networks—in other words, the internet—to send data collected from IoT-connected devices to its destination. So the main distinction between the two is the method of communication/connection: wired, cellular, or wireless for M2M vs. just wireless for IoT.
M2M Technology Requirements
Any M2M technology or protocol needs to have many characteristics, too many to mention in full here. But one major requirement is scalability. The system has to be able to grow and allow new devices to join as needed.
M2M devices and systems also need to be able to log certain information about their processes. Since M2M uses automation instead of human intelligence, if there’s a problem, the system needs to log it in order for anyone to notice and address the issue.
Finally, for security purposes, devices in an M2M system should have the capability of being anonymous. In other words, they should be able to hide certain information from other devices and systems. This is to prevent devices from being easily accessed by outsiders.
Real World M2M Applications
One of M2M’s ongoing goals is to allow easier and more direct access to data. M2M technology and apps work to facilitate that goal.
One of the top use cases for M2M is remote monitoring, for example, when M2M communication is used as part of warehouse management systems (WMS) and supply chain management systems (SCMS), the systems allow companies to track inventory at a glance. Both WMS and SCMS use sensors to keep track of where everything is and send that data to a central system through M2M communication for you to see.
Another example is security monitoring. In an IoT security system, you can monitor and control your home security from anywhere with your smartphone based on the M2M communication between the IoT security devices and your phone.
Also, the healthcare industry uses M2M for telemedicine. For example, patients can measure their own vitals at home and have the data automatically transferred machine-to-machine to their personal physicians’ office systems.
Energy and utility companies use smart meters to monitor energy usage and detect leaks. They can often discover areas where maintenance might be required down the road and, through M2M, send an alert to your device to tell you there’s a need for preventative maintenance. For example, if a sensor detects overly high pressure in a particular part of a system, that part could break down faster and require replacement sooner. Replacing things early means you won’t have as much downtime.
Smart home apps allow various home appliances to communicate with each other. For example, you could use an app on your phone and set your smart coffeemaker to turn on right as your smart alarm clock goes off. Or an entry sensor in your home security system could communicate with your home alarm and send an alert to your phone to warn you of an intruder.
M2M Standards
Now that we understand how M2M systems work, we can get further into the nitty-gritty of what these applications need in order to function: namely, the protocols and standards they use to provide M2M connectivity.
Firstly, you should realize that many M2M systems are built to be task- or device-specific. That means that they’re not necessarily interoperable, so one system won’t necessarily be able to communicate with another because of the differences in standards. This is particularly true of SCADA systems, but it also applies to many IoT systems.
For example, the Message Queue Telemetry Transmission (MQTT) protocol allows devices to communicate in an M2M system. It’s ideal for certain IoT use cases in which reliability is paramount, as is true in industrial IoT systems. MQTT also requires little energy compared to many other protocols. But it doesn’t work for video streaming, so using MQTT for smart cameras is out of the question. MQTT can have some issues with latency and low speed, since all communication has to go through the cloud server layer. Plus, MQTT doesn’t have native encryption and security features, and it still isn’t lightweight enough for the lowest-powered devices.
By contrast, the Constrained Application Protocol (CoAP) is perfect for devices that have little energy to spare. CoAP is lightweight and can be encrypted with the data transport layer security (DTLS) model, which is highly secure. But CoAP is not as reliable as MQTT, especially when dealing with different firewalls. Nabto Edge solves that problem by tunneling right through firewalls and providing the DTLS encryption required to make CoAP a top protocol for lightweight IoT devices. But CoAP doesn’t work for devices that need a lot of power and reliability.
Moving beyond IoT, M2M can also use the hypertext transfer protocol (HTTP), an internet protocol encrypted with secure socket layer (SSL) or transport layer secure (TLS) models. Though HTTP is quite a bit heavier than either of the other two protocols, meaning it requires more power and memory. This is why HTTP is rarely used in IoT.
Finding a way for devices that use different protocols to communicate within a system is both a challenge and a major goal of well-applied M2M technology.
The Bottom Line
All in all, IoT is just one application of M2M. However, IoT is also one that’s replacing or enhancing many earlier applications and systems and improving the efficiency of gathering and processing data plus controlling systems remotely. M2M is constantly evolving, and it will be exciting to see where it goes in the future.
Read Our Other Resources
We’ve also published a range of IoT resources for our community, including:
- Discover Five IoT Trends to Look Out for in 2022.
- Learn more about The Latest IoT Applications for Smart Buildings: Trends and Benefits
- Learn about P2P connectivity through our P2P Explainer.