The world of IoT is getting bigger and bigger.
And while this makes our lives much easier, it’s also leaving our personal information and data privacy at risk.
You may be reading this and wonder why security and privacy in IoT are so important? Well, the more we’re connected to the world of the Internet of Things, the more we surrender our data privacy and risk our online security. Most of the time, without knowing it!
So, as an IoT developer, what can you do? It’s true that IoT privacy and security risks aren’t going anywhere. However, there are some best practices you can incorporate into your IoT device to protect yourself and your users to overcome these threats.
What Are The Biggest Threats to Security and Privacy IoT?
Before we look at the best ways of protecting your IoT application, we’re going to go over the biggest threats or, in other words, the causes for data breaches and attacks on IoT devices.
Lack of Compliance From IoT Manufacturers or Developers
At this moment in time, there is a lack of universal IoT security standards. As a result, some IoT manufacturers or developers don’t prioritize device or user security. Furthermore, it leaves the door open to corporate spying.
This will remain one of the biggest security issues within the world of IoT until there are universal standards and regulations that manufacturers have to comply with. Make sure you’re one of the good guys, and don’t go down this path.
Users Lack Understanding and Knowledge of IoT Security
Over the years, the general population has come up to speed with threats on the internet. Whether that’s learning how to avoid spam or phishing emails or securing WiFi connections with strong passwords (well, maybe that could use some practice).
However, IoT is still a relatively new technology. You can hardly accuse the average user of being reckless if they know little about it. This puts everyone at risk. IoT users’ ignorance and lack of awareness of IoT functionality don’t just affect them; it affects everyone who may have inadvertently or intentionally connected to their device.
This highlights the importance of IoT manufacturers to protect users from themselves and implement good quality security and privacy protections.
Poor Device Update Management
Insecure software or firmware are more security and IoT privacy concerns. Of course, manufacturers originally sell devices with the latest software update. That being said, in the fast-moving online world, it’s inevitable that new vulnerabilities will surface over time.
These can be avoided by regularly updating IoT devices when a new version becomes available. However, this is often neglected. While smartphones and laptops can remind users and carry out automatic updates, some IoT devices continue running without the necessary updates to combat new security threats.
Rogue IoT devices
The IoT world is awash with new devices. In fact, it’s predicted that that number will hit 18 billion by 2022. This is great for IoT hobbyists, but unfortunately, rogue or malicious IoT devices can be installed to secured networks without authorization.
A rogue device replaces the original one or integrates as an IoT network protocol to collect or alter sensitive information between devices. For example, they could be turned into rogue video cameras (e.g., the Raspberry Pi being used for app access) or intercept incoming data behind users’ backs.
Tips for Keeping Your Users Safe and How to Overcome Their IoT Privacy Concerns
If you’re committed to overcoming these IoT Privacy challenges and keep users’ safe, check out these IoT privacy solutions.
Secure Your IoT Network
To avoid interceptions from rogue devices or other potentially harmful cyber attacks, you need to protect and secure the network that’s connecting various IoT devices.
This is one of the most straightforward on the list as it just touches on security measures that everyone hopefully already follows online. The traditional endpoint security you use should include:
- Antivirus
- Anti-malware
- Firewalls
Of course, this is the bare minimum and step one for a reason. So don’t stop here!
Use IoT Data Encryption
If you’re serious against protecting the privacy of users and preventing data breaches, you need to encrypt the data at both rest and in-transit between IoT devices.
This can be done by using IoT encryption algorithms. Whether the keys you use are symmetric or asymmetric, this is an important step in protecting users.
Test, Test and Keep Testing (and Updating)
IoT devices need proper testing throughout their lifecycle. That means before it’s released to the public and while it’s on the market.
As mentioned before, smartphones and laptops circumvent this through automatic updates. However, IoT manufacturers often fall foul by rarely providing updates or none at all. This is a dangerous game. It only takes one serious breach for you to lose customers or your reputation. So, if you want your IoT device to have longevity, regularly test and update.
Authenticate IoT Devices
As well as using encryption keys to protect users, you also should allow users to authenticate IoT devices.
This is done by introducing some multiple user management features for a device and then implementing mechanisms, such as:
- Two-factor authentication
- Digital certificates
- Biometrics
Learn more about the different IoT Device Authentication Methods here.
PRO TIP: Use a Decentralized IoT Solution
While the tips above can certainly help protect your users’ IoT security and IoT data privacy, there’s an extra step that many IoT manufacturers miss. This is the choice of IoT Application Enablement Platform (AEP).
The “traditional” AEP solution (such as AWS IoT or Microsoft Azure) stores data centrally in the cloud. The issue here is the inherent vulnerability of data in centrally stored databases.
A user’s personal data isn’t necessarily stored for a long term in a central database. However, it passes through a relay in cleartext. This means it’s not encrypted end-to-end, and your personal data is still vulnerable. See what we mean below:
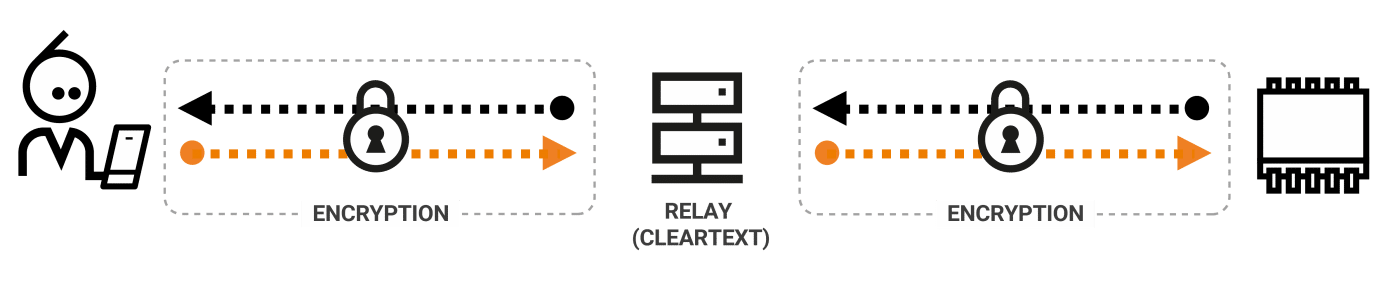
However, in a decentralized AEP, such as a P2P platform, data flows directly between the client and the IoT device, and all data is stored securely in the IoT device rather than the cloud.
This allows the user to have complete control over the data residing on their network, and, therefore, the risk of a third party intercepting data is almost eradicated.

Here at Nabto, our IoT Application Enablement Platform uses peer-to-peer connectivity to decentralize data processing and storage, therefore removing many of the security vulnerabilities of traditional AEPs.
Find out more about how Nabto’s IoT platform can offer your user’s more robust privacy and security here.
Stay Up to Date and Stay Vigilant
As you can see, the larger the world of IoT becomes, the greater the importance of prioritizing IoT data privacy and security.
Unfortunately, cyber-attacks and rogue devices will not go anywhere, and they will only get smarter. Therefore, we recommend you remain up to speed with the latest attacks and always keep working on providing the best security and privacy features you can. This not only helps you guard against data breaches it also builds confidence and trust in your product.
If you want to learn more about Nabto IoT Solutions – or simply want to hear what we recommend for your IoT device – get in touch with us today.
Read Our Other Resources
We’ve published a range of IoT resources for our community, including:
- A Comparison of IoT Protocols, which provides a complete comparison of the major protocols and standards available.
- Buying versus building an IoT platform, which discusses how to choose the best option for you.
- Our guide on how to Develop IoT Apps and what platforms you can use.
- Find the right microcontroller by reading our Complete Guide to Microcontrollers for IoT.