You’ve probably heard of several cases involving digital privacy issues such as customer data leaking, GDPR breaches, or general lack of cybersecurity. This only stresses the importance of considering the level of privacy in an IoT solution – not only to increase end-user confidence and willingness to invest in an IoT-enabled device, but also to decrease the risk for the IoT device vendor.
Watch the video below to get a quick overview of the importance of privacy.
Two types of connection – two levels of privacy
Today there are, roughly speaking, two types of IoT application platforms: the traditional server-based IoT solution and the decentralized IoT solution with data on the edge. Let’s look more closely into these two and their level of privacy:
When using an IoT solution you are working with some sort of data – whether it is streaming of video, commands, notifications of device activity, audio, etc. This data is sent and received between the client (an app on your smartphone, tablet, or computer) and the IoT device.
In a traditional server-based IoT solution, you have a centralized data store in the infrastructure where the server application stores data: Data is transmitted between client and server and between server and device. Numerous stories have been reported about leaks of such centrally stored data either due to poor security design or rogue administrators with access to the central data store.
In a decentralized IoT solution, data flows directly between the client and the IoT device, and all data is stored on the IoT device. Typically, you use peer-to-peer (P2P) techniques to establish this type of connection; it yields maximum performance and enables the user to have full control over the data residing on their own network. With a solid security model, the risk of a third-party accessing it is minimized. This also makes it much easier for the vendor to avoid trouble with the EU’s GDPR (General Data Protection Regulation) as the personal information of the user isn’t stored on a central server – it is stored by the user on a user-owned device.

Decentralized IoT solution
Secure, direct connectivity through a P2P connection from client to IoT device
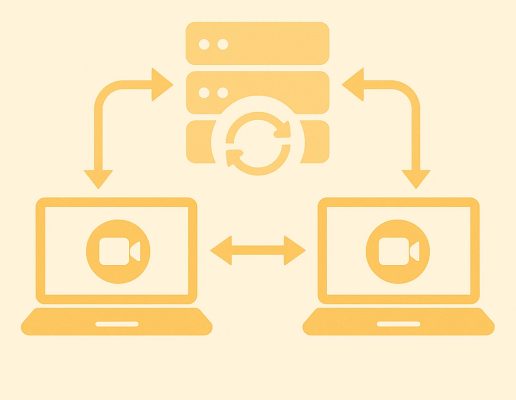
In a P2P-based connection, the data is directly transmitted with end-to-end encryption. Many of the big players (for example Amazon AWS and Microsoft Azure) also use relaying of data, where data travels from client to IoT device through the cloud server. In this scenario, the data isn’t stored on the server but passes through the relay in cleartext, which means it is not encrypted end-to-end (see the illustration below).

Traditional server-based IoT solution
using relaying of data

Decentralized IoT solution
with end-to-end encryption/ the Nabto platform
Which approach to choose?
If privacy, usability and performance are the only concerns, a decentralized IoT solution using P2P principles for direct connectivity is the simple choice. But, some vendors also need centralized processing of data for “traditional” big data purposes.
Hence, a combined solution could be ideal where you get the best of both worlds – the decentralized approach for best interactive performance and most data stored on the edge, on the user’s network, with only a subset of data pushed as necessary to the centralized big data solution.
In some IoT scenarios, the interactive experience is not important, and it is only relevant with central analysis of data. Here it makes sense to push all data to the central solution for processing – despite the privacy challenges.
Get high privacy with the Nabto IoT platform
The Nabto IoT platform is a high-performing P2P solution with direct connectivity that might be a great choice for you if you want to ensure your customers’ privacy. Do not hesitate to set up a free consultation with one of our IoT experts and learn more about how you can use direct connectivity for your IoT solution.